Google Authenticator crea códigos de verificación en dos pasos en tu teléfono para proporcionar un extra de seguridad en determinados servicios, ya sea nuestra cuenta de Google, Dropbox…o en este caso las conexiones por SSH en Linux.
Lo primero que deberemos hacer es instalar el módulo Google Authenticator :
apt-get install -y libpam-google-authenticatorUna vez instalado debemos habilitar el módulo añadiendo la siguiente línea dentro del fichero /etc/pam.d/sshd
auth required pam_google_authenticator.soDespués de haber guardado los cambios anteriores debemos buscar la línea ChallengeResponseAuthentication no dentro del fichero /etc/ssh/sshd_config. Debemos modificar el parámetro «no» cambiándolo por «yes»:
ChallengeResponseAuthentication yesReiniciamos el servicio de SSH:
sudo service sshd restartUna vez realizado todo lo anterior debemos iniciar Google Authenticator y vincularlo con la app.
Introducimos el siguiente comando para comenzar la configuración:
google-authenticatorRespondemos «yes» a las preguntas que nos vaya generando la configuración inicial para la autenticación en dos pasos:
Do you want authentication tokens to be time-based (y/n) y
Warning: pasting the following URL into your browser exposes the OTP secret to Google:
https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/pi@raspberrypi%3Fsecret%3D2GKX7AOBQIOSTMSCCMOZDN36DE%26issuer%3Draspberrypi
Your new secret key is: 2GKX7AOBQIOSTMSCCMOZDN36DE
Your verification code is 734288
Your emergency scratch codes are:
99939999
41896199
15563930
78539836
88322167
Do you want me to update your "/home/pi/.google_authenticator" file? (y/n) y
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases
your chances to notice or even prevent man-in-the-middle attacks (y/n) y
By default, a new token is generated every 30 seconds by the mobile app.
In order to compensate for possible time-skew between the client and the server,
we allow an extra token before and after the current time. This allows for a
time skew of up to 30 seconds between authentication server and client. If you
experience problems with poor time synchronization, you can increase the window
from its default size of 3 permitted codes (one previous code, the current
code, the next code) to 17 permitted codes (the 8 previous codes, the current
code, and the 8 next codes). This will permit for a time skew of up to 4 minutes
between client and server.
Do you want to do so? (y/n) y
If the computer that you are logging into isn't hardened against brute-force
login attempts, you can enable rate-limiting for the authentication module.
By default, this limits attackers to no more than 3 login attempts every 30s.
Do you want to enable rate-limiting? (y/n) yEscaneamos el código BIDI con la app Google Authenticator y observaremos que se generan códigos temporales para la autenticación en dos pasos:
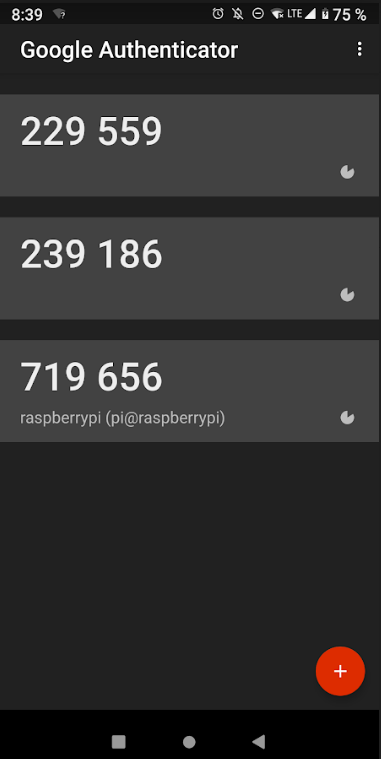
Probamos a conectarnos por SSH y comprobaremos que tras logarnos con el usuario y contraseña nos solicitará el código de verificación donde introduciremos el código que este visible en ese momento en la app Google Authenticator.
Login:pi
Password:
Verification code:
Linux raspberrypi 4.19.75-v7+ #1270 SMP Tue Sep 24 18:45:11 BST 2019 armv7l
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Oct 30 07:15:26 2019 from
pi@raspberrypi:~ $