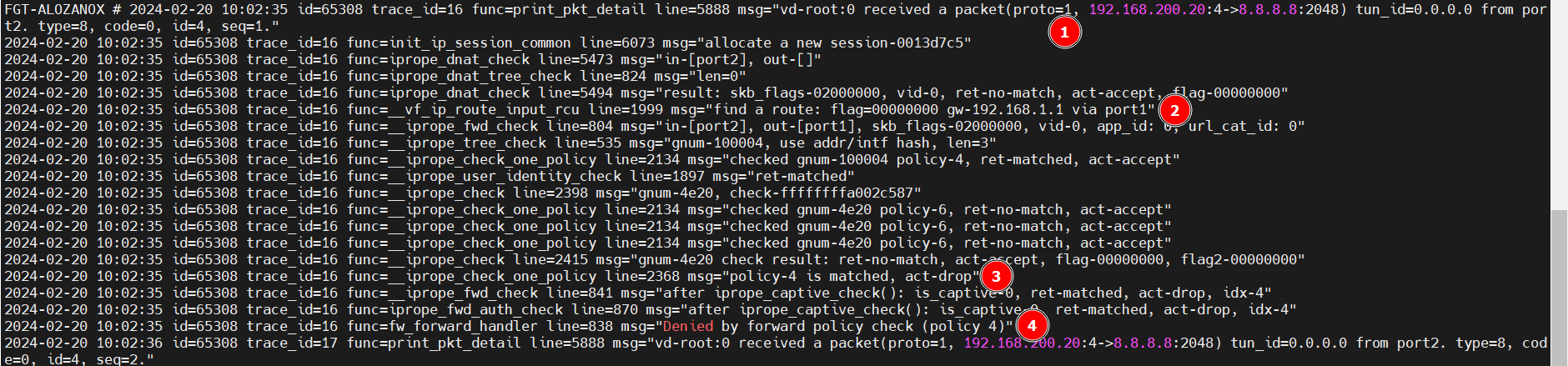
En muchas ocasiones como administrador de redes necesitaremos monitorizar o «esnifar» el tráfico en un firewall (en este caso un Fortigate) para realizar tareas de troubleshooting.
A continuación vamos a poner algunos ejemplos de comandos útiles con el objetivo de filtrar el tráfico para comprobar si la comunicación se está estableciendo correctamente.
- Monitorizar tráfico por IP: diagnose sniffer packet any ‘host 172.24.128.138’ 4
fortigate# diagnose sniffer packet any 'host 172.24.128.138' 4
interfaces=[any]
filters=[host 172.24.128.138]
port3 in 172.24.126.107.5666 -> 172.24.128.138.38426: psh 471564832 ack 2541045057
port5 out 172.24.126.107.5666 -> 172.24.128.138.38426: psh 471564832 ack 2541045057
port5 in 172.24.128.138.38426 -> 172.24.126.107.5666: psh 2541045057 ack 471565897
port3 out 172.24.128.138.38426 -> 172.24.126.107.5666: psh 2541045057 ack 471565897
port5 in 172.24.128.138.38426 -> 172.24.126.107.5666: fin 2541045088 ack 471565897
- Monitorizar tráfico entre dos IP’s: diagnose sniffer packet any ‘host 172.24.128.138 and host 172.24.126.175’ 4
fortigate # diagnose sniffer packet any 'host 172.24.128.138 and host 172.24.115.131' 4
interfaces=[any]
filters=[host 172.24.128.138 and host 172.24.115.131]
port5 in 172.24.128.138.37996 -> 172.24.115.131.1532: syn 853903031
port3 out 172.24.128.138.37996 -> 172.24.115.131.1532: syn 853903031
port3 in 172.24.115.131.1532 -> 172.24.128.138.37996: syn 1321500846 ack 853903032
port5 out 172.24.115.131.1532 -> 172.24.128.138.37996: syn 1321500846 ack 853903032
port5 in 172.24.128.138.37996 -> 172.24.115.131.1532: ack 1321500847- Monitorizar tráfico entre dos IP’s y puerto: diagnose sniffer packet any ‘host 172.24.128.138 and host 172.30.33.143 and tcp port 5666’ 4
fortigate # diagnose sniffer packet any 'host 172.24.128.138 and host 172.30.33.143 and tcp port 5666' 4
interfaces=[any]
filters=[host 172.24.128.138 and host 172.30.33.143 and tcp port 5666]
port5 in 172.24.128.138.51826 -> 172.30.33.143.5666: syn 2429771618
port6 out 172.24.128.138.51826 -> 172.30.33.143.5666: syn 2429771618
port6 in 172.30.33.143.5666 -> 172.24.128.138.51826: syn 690107217 ack 2429771619
port5 out 172.30.33.143.5666 -> 172.24.128.138.51826: syn 690107217 ack 2429771619
port5 in 172.24.128.138.51826 -> 172.30.33.143.5666: ack 690107218